It’s been said that when it comes to phishing and malware, there are two kinds of people—those who know they’re victims, and those who don’t. Last week’s Tip post, Small Business Security: Focus on a Speedy Recovery, detailed measures you can take to mitigate the damage in the (unfortunately very likely) event that your small business finds itself compromised by ransomware or other malware, or finds that an employee has been tricked into disclosing credentials.
That’s the pound of cure. This week we’ll focus on the ounce of prevention. After all, it is far better to detect a phishing email before you download a malicious attachment or click a link leading to a phishing page. And in the event that you don’t catch yourself before you click, it is critical that you pay attention to browser warnings and other signs that you are on a phishing screen rather than a legitimate website.
Studies Show Consistent Problems with Identifying Phishing Email
That message has been getting through loud and clear, thanks to relentless reminders by company security teams, online security evangelists, the media, and blog posts like this one. The problem is that people have a hard time identifying phishing email. And to make matters worse, they often end up discarding legitimate (and possibly important) email out of the fear that it is malicious.
How are you accepting payments?
Learn all the ways to accept online payments
Click here to access the FREE [Cheat-Sheet]
A recent study asked participants to evaluate 40 emails, told them that some were phishing, and asked them to classify each as legitimate or phishing. The Results: 44% of Phishing Emails were identified as Legitimate and 24% of Legitimate Emails were identified as Phishing.
Another study found that when shown legitimate email from a colleague asking them to edit a shared document, 35.4% of participants falsely identified it as phishing. The same study found that 17.7% of participants incorrectly labeled alerts about online banking statement availability as phishing, and 11.3% of participants labeled a merchant’s legitimate email regarding an expired credit card as phishing.
Eliminate the Obvious and Scrutinize the Rest
So while the standard advice is to always err on the side of caution (good advice indeed), as a small business owner you need to balance that with a need for your business to run smoothly. The best way to do that is to educate your team so that they become better at identifying phishing and other malicious email so that false alarms are minimized.
You can probably trust that your team is not going to give away the store to a businessman from the Isle of Man promising a $1M order, or the chance to act as his “agent” for a money transfer out of the country. (Yes, I got an email just like that yesterday.)
They are probably already well trained enough to spot the obvious signs of phishing such as urgent calls to actions, forms asking for credentials in the email, spoofed FROM addresses, and unexpected attachments. They probably also know to hover over links to inspect the destination before clicking, and to make sure they are on a secure “https” page before submitting any personal information.
Where you and your team are likely to slip-up is when clever phishers use advanced techniques to fool even a vigilant target. Watch for the following:
Email Tricks: Adding Noise to Text
Spam filtering programs and services are designed to look for large numbers of messages that use the exact same text or link to the exact same place. The services use giant databases of messages collected from around the world to identify these patterns. To help avoid detection, spammers/phishers try to make each email look unique to spam filters. However, by doing this they leave telltale clues in the message source that you can use to identify a message as spam or phishing.
Common Methods:
- HTML code for small letters and/or white text.
For example the following html code:
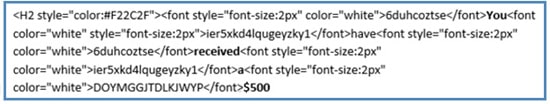
looks like the following in the email message
You received $500
- Text with a No-Display Tag
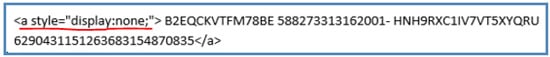
- Text with 0 Font

Easy Detection Technique:
If you suspect phishing, check the email source, scroll through the header and in the body look for any of the “Noise” tricks.
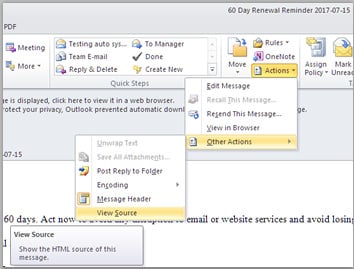
To do this in Microsoft Outlook, with the email open select Actions–>Other Actions–>View Source.
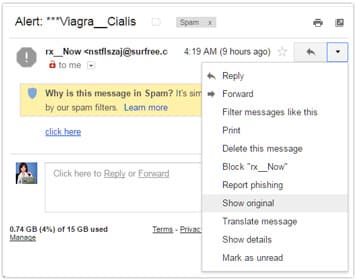
In Gmail, select “Show Original” from the Actions menu.
Link Tricks: Adding Noise to Links
Adding noise to URLs behind links is another technique spammers use to trick email filters. When the link is clicked, the extraneous text is ignored and it resolves correctly.
57 Sales Tips That Actually Work!
From the President of PaySimple to You: The Small Business Sales Guide
Click here to access the FREE guide
Common Methods:
(In the following examples, the real part is in green and the subterfuge in red)
- Adding extraneous characters that are ignored
http://goo.gl////////nnnnn…../././././././////…fff/v5u397 - Including a well known site in a comment
http://goo.gl/<!–trustedsite.com/login.html–>v5u397 - Adding non-existent parameters to the end of a link
https://vms.com/gotcha?amazon.com/claim_prize.html - Using leading text that will be ignored
https://paysimple.com/login/@vms.com/gotcha.php
(The @ is for user validation, which most sites no longer use. Anything preceding it will be ignored when the link resolves.)
Easy Detection Technique:
Always check link destination before clicking, and watch for these tricks. To do this, hover over links in a desktop or laptop environment to view the destination before you click.
On a mobile device, tap and hold to see where the link goes before actually accessing the page. The video below is for an iOS device, Android functions similarly.
Link Tricks: Domains Designed to Deceive
Phishers take advantage of the brain’s tendency to see what it expects, rather than what it actually there. To do this, they register valid domains that can be used to fool targets, especially when they are not paying close attention.
Common Methods:
- Registering a domain that includes “com-” and using it with a subdomain.
(The phishing domain is in red, the subdomain subterfuge is in green)
paysimple.com-vms.ru/login
- Registering a lookalike (or look very close) domain
PAYSlMPLE.COM
(the red letter is a lowercase “L”; top-level domains are not case sensitive)
- Using a top-level domain to deceive
(in most cases our brains will not see the misplaced “dot”)- trustedcompanyc.om (.om is the domain for Oman)
- redcrosso.rg (rg is the domain for Republic of Guy)
- yalee.du or yale.du (du is the domain for Duteshlund)
Easy Detection Technique:
While you can catch this trick if you look very closely at FROM email addresses and link destinations, it is very easy to fall victim. The good news is that once you land on a phishing page using this type of domain, unless the phisher went to quite a bit of trouble, it will not have a valid security certificate. If that’s the case, your browser bar will warn you.
Before entering credentials, financial account information, or any other type of personal information look for “https” and a trusted lock symbol. Beware of red warnings and even gray neutrals.
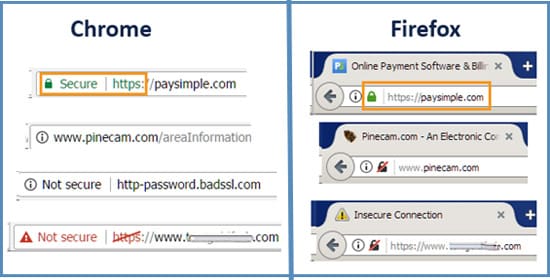
Link Tricks: URL Shortening
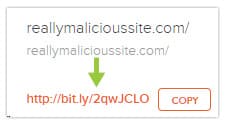
URL shortening services such as bit.ly, goo.gl, and tinyurl.com are often used in social media posts where characters are restricted and in emails or other marketing communications where long links would be visually unattractive. Unfortunately, the malfeasants have glommed onto URL shortening as a simple way of tricking you into thinking that a malicious link is safe.
This technique is amazingly easy. Just go to one of these services, enter in a long malicious URL, and get a short sanitized URL that will not alarm anyone.
Easy Detection Technique:
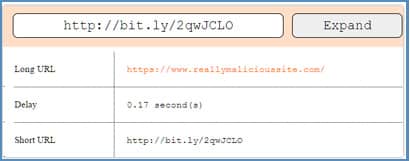
You could simply refuse to click any shortened URLs, but in today’s world that would cause you to miss tons of important legitimate content. A better way is to use a tool like checkshorturl.com, or to use an extension in your Chrome or Firefox browser that shows the real link destination when you right-click a shortened URL.
With the checkshorturl.com tool, not only will you see the actual link destination (as shown below), you will also see information about the real destination, including whether it has been reported as malicious.
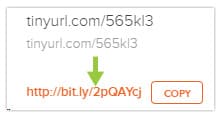
A Detection Counter-Measure
While this defense may work, a sophisticated hacker can get around it by putting shortened URLs into other shorteners multiple times. Even if you tried to decode each one in turn, you might never get to the actual end.
Practice Makes Closer to Perfect
The phishing tricks outlined above are just some of the many nefarious techniques scammers have in their toolbox. But, the more you know the better prepared you will be when you face your inbox each and every morning. And, the more experience you have with identifying phishing and other malicious email, the better you’ll be at it, and the more confident you’ll feel about the judgements you make.


